Introduction to Cracking MD5 Encryption- Breaking the Hash Functions :
You may often heard this word "MD5 Hash". If you don't know what it is, this post may help you. If you know about MD5 Algorithm, you can skip to Cracking MD5 Encryption Section. In this article i will explain clearly what MD5 Hash
Introduction to MD5 Algorithm:
you can refer this link Introduction To Cryptography ,if you don't know about encryption.
MD5 is widely used Hash Algorithms by Website owners. MD5 was designed by Ron Rivest in 1991 to replace an earlier hash function, MD4.
It is not like usual encryption. Usually we encrypt the original text to cipher text then decrypt the cipher text to original text.
we can call the MD5 as "One Way Encryption"(No longer).
It is like one way path. one can move to destination but can not come back to starting place.
Encrypt(originalText)
Decrypt(cipherText)
It will be converted to
Algorithm:
MD5 processes a variable-length message into a fixed-length output of 128 bits. The input message is broken up into chunks of 512-bit blocks (sixteen 32-bit little endian integers); the message is padded so that its length is divisible by 512. The padding works as follows: first a single bit, 1, is appended to the end of the message. This is followed by as many zeros as are required to bring the length of the message up to 64 bits fewer than a multiple of 512. The remaining bits are filled up with a 64-bit integer representing the length of the original message, in bits.
The main MD5 algorithm operates on a 128-bit state, divided into four 32-bit words, denoted A, B, Cand D. These are initialized to certain fixed constants. The main algorithm then operates on each 512-bit message block in turn, each block modifying the state. The processing of a message block consists of four similar stages, termed rounds; each round is composed of 16 similar operations based on a non-linear function F, modular addition, and left rotation. Figure 1 illustrates one operation within a round. There are four possible functions F; a different one is used in each round:
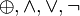 denote the XOR, AND, OR and NOT operations respectively.
denote the XOR, AND, OR and NOT operations respectively.
MD5 HASHES:
The 128-bit (16-byte) MD5 hashes (also termed message digests) are typically represented as a sequence of 32 hexadecimal digits. The following demonstrates a 43-byte ASCII input and the corresponding MD5 hash:
The hash of the zero-length string is:
Boer Showed that MD5 is executed on 1 block of 512 bits will yield the same output for different input values in the buffer ABCD. This is known as Pseduo Collision.
Berson said Differential crypt analysis, with in a reasonable time to find 2 messages that produce this same hash code.
Dictionary Method on MD5:
In dictionary method the hash code will compared with some usual passwords.
For Eg: Users may give simple and usual password like "love","iloveyou".
Convert this usual words to Hash code.
Then store the words to Dictionary.
Compare User's Hash code with each hash code which is listed in dictionary.
Birthday Attacks On MD5:
Name itself define the attack method. You alone birth on your birthday? The answer is negative, there are lot of people born on your birthday. The same method is used here. Some of original text will use same Check Sum.
Introduction to MD5 Algorithm:
you can refer this link Introduction To Cryptography ,if you don't know about encryption.
MD5 is widely used Hash Algorithms by Website owners. MD5 was designed by Ron Rivest in 1991 to replace an earlier hash function, MD4.
It is not like usual encryption. Usually we encrypt the original text to cipher text then decrypt the cipher text to original text.
we can call the MD5 as "One Way Encryption"(No longer).
It is like one way path. one can move to destination but can not come back to starting place.
Encrypt(originalText)
Using MD5 Hash algorithm we can only create a hash code. Original Text is converted to 128 bits hash code(encrypted form).Consider my original text is "BreakTheSec".
It will be converted to
4258118ee03eb6996adb71a59e1c6d09
Algorithm:
MD5 processes a variable-length message into a fixed-length output of 128 bits. The input message is broken up into chunks of 512-bit blocks (sixteen 32-bit little endian integers); the message is padded so that its length is divisible by 512. The padding works as follows: first a single bit, 1, is appended to the end of the message. This is followed by as many zeros as are required to bring the length of the message up to 64 bits fewer than a multiple of 512. The remaining bits are filled up with a 64-bit integer representing the length of the original message, in bits.
The main MD5 algorithm operates on a 128-bit state, divided into four 32-bit words, denoted A, B, Cand D. These are initialized to certain fixed constants. The main algorithm then operates on each 512-bit message block in turn, each block modifying the state. The processing of a message block consists of four similar stages, termed rounds; each round is composed of 16 similar operations based on a non-linear function F, modular addition, and left rotation. Figure 1 illustrates one operation within a round. There are four possible functions F; a different one is used in each round:
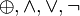 denote the XOR, AND, OR and NOT operations respectively.
denote the XOR, AND, OR and NOT operations respectively.MD5 HASHES:
The 128-bit (16-byte) MD5 hashes (also termed message digests) are typically represented as a sequence of 32 hexadecimal digits. The following demonstrates a 43-byte ASCII input and the corresponding MD5 hash:
MD5("The quick brown fox jumps over the lazy dog")
= 9e107d9d372bb6826bd81d3542a419d6
The hash of the zero-length string is:
MD5("")Refer For More
= d41d8cd98f00b204e9800998ecf8427e
Cracking MD5 Hash Algorithm:
In 1996, World comest to know that there are some flaws in MD5 HASH Algorithm. Cryptographers began recommending the use of other algorithms, such as SHA-1 (which has since been found also to be vulnerable).Boer Showed that MD5 is executed on 1 block of 512 bits will yield the same output for different input values in the buffer ABCD. This is known as Pseduo Collision.
Berson said Differential crypt analysis, with in a reasonable time to find 2 messages that produce this same hash code.
Dictionary Method on MD5:
In dictionary method the hash code will compared with some usual passwords.
For Eg: Users may give simple and usual password like "love","iloveyou".
Convert this usual words to Hash code.
Then store the words to Dictionary.
Compare User's Hash code with each hash code which is listed in dictionary.
Birthday Attacks On MD5:
Name itself define the attack method. You alone birth on your birthday? The answer is negative, there are lot of people born on your birthday. The same method is used here. Some of original text will use same Check Sum.
How to Crack MD5?
You don't need to write algorithm to crack the MD5. There are plenty of websites available to crack the MD5.I have listed the list of websites in my previous post.
Refer thEsE link:




No comments:
Post a Comment